On September 17, 2025, the extremely exciting and high-profile “Optical & Digital Document Security Conference” concluded, where Ara-Authentic also had the opportunity to present its latest exhibits on the topic of anti-counterfeiting.
During this conference, the IOTA (International Optical Technologies Association) also presented awards in seven categories.
The award for the best product security application went to Ara-Authentic, which we were very pleased about.
Specifically, our concept was awarded, which consists of counterfeit-proof, additive, “always warm” ARA-checkmyheat® product markings, as well as equally counterfeit-proof labels on their outer packaging. These are correlated with each other and can be quickly and reliably verified for authenticity using one’s own smartphone.

Our Technology
Using the vacuum-based coating process known as Physical Vapour Deposition (PVD), a thin inorganic layer is applied to a transparent, flexible PET carrier film.
The PET film coated in this way is then placed with its PVD side onto the product surface, stretched over it, or, in its self-adhesive version, fixed in the focal plane of a standard marking laser.
With suitably adjusted laser parameters, the activation of the laser beam causes the PVD layer to be transferred from the PET film to the product surface, simultaneously implementing the specific, counterfeit-proof properties.
Both the PVD processes and the interaction of the PVD layer with the laser beam can generate properties and functionalities within the layers that are simply not possible with other coating methods. Specifically, this means that the creation of the laser layers is not subject to thermochemical equilibrium conditions.
The counterfeit protection is ensured by the fact that both the process settings during the production of the laser films and the exact laser settings for the laser-induced markings—which are in turn adapted for the specific product surface—must be precisely known.
It is not possible to re-engineer the laser-applied, counterfeit-proof layers.
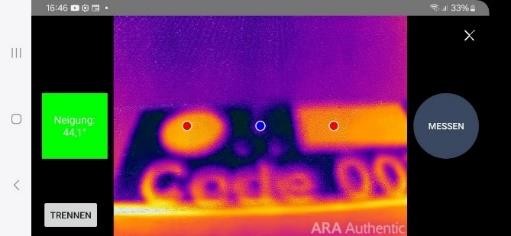
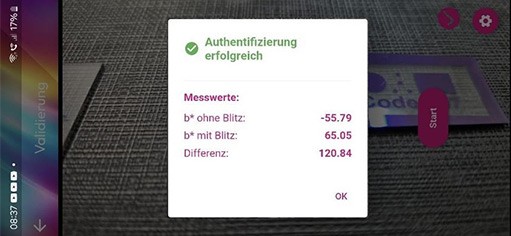
The method of authentication is determined in consultation with the customer and can be done, for example, with a smartphone.
Additional information can also be integrated into the counterfeit-proof marking, for instance, in the form of a Data Matrix code that is itself designed to be counterfeit-proof but can be read like a “normal code” with standard commercial apps.